In an era where cyber threats are constantly evolving and attacks are becoming more sophisticated, organizations need a central tool to understand and address their security exposures. Defender Security Exposure Management is just that tool – a unified portal that provides a real-time view of risks and helps prioritize key security actions.
What is Defender Security Exposure Management?
This new feature is designed to give organizations a real-time view of their security risks and exposures. Rather than focusing solely on known vulnerabilities and patches, Defender Security Exposure Management analyzes the broader security landscape and prioritizes actions based on real risk.
Microsoft has already structured a number of initiatives that bring together key security areas so organizations can quickly identify and address the most critical exposures. These initiatives cover areas such as Endpoint Security, Identity Security, Ransomware Protection, and Zero Trust, providing a unified and strategic approach to security management.
Why is this important?
Traditionally, security teams have worked with static lists of vulnerabilities and compliance requirements. But with the speed at which the threat landscape is evolving, it’s not enough to follow a list from last quarter—organizations need real-time insight and risk-based prioritization.
With Defender Security Exposure Management, you can:
- Understand and address the most critical security risks first.
- Minimize the risk of becoming a target for targeted attacks.
- Streamline security efforts by reducing the noise of less critical alerts.
How does it work?
Defender Security Exposure Management integrates directly into Defender for Endpoint and works with a combination of:
- Threat intelligence from Microsoft’s extensive security data.
- Context-based analysis that takes into account the organization’s unique environment.
- Automated action where recommended actions can be implemented directly from the portal.
Attack Path Management in Defender Security Exposure Management
A key feature of Defender Security Exposure Management is Attack Path Management, which allows organizations to identify and visualize potential routes that attackers can exploit to compromise critical assets. By analyzing the correlation between different assets and vulnerabilities, this feature helps understand how an attacker can move through the network to achieve their goals.
Key features of Attack Path Management:
- Attack Path Dashboard: Provides an overview of all identified attack paths in the organization, including the number of attack paths, choke points, and critical assets. This helps understand the organization’s security posture and prioritize security efforts.
- Choke Points: Identifies key assets where multiple attack paths intersect, making them critical vulnerabilities. By focusing on these choke points, security teams can effectively mitigate risk by addressing high-impact assets and preventing attackers from advancing through multiple paths.
- Blast Radius: Enables visualization of how compromising one asset can impact other parts of the network. This helps assess the broader consequences of an attack and prioritize mitigation strategies more effectively.

By implementing Attack Path Management, organizations can shift from a reactive to a proactive security strategy, where they not only focus on individual vulnerabilities, but also understand and disrupt potential attack paths before they are exploited.

Key initiatives in Defender Security Exposure Management
To provide a structured view of an organization’s security posture, Microsoft has brought together a set of initiatives in Defender Security Exposure Management. These initiatives target key security areas and help prioritize efforts across identity, endpoints, IoT, cloud, and Zero Trust strategies.
- Endpoint Security
- Identifies vulnerable configurations on clients and servers.
- Provides recommendations for improved endpoint patching and hardening.
- Enterprise IoT Security
- Monitors connected devices for security risks and unknown activity.
- Secures IoT devices with policy-based restrictions and threat isolation.
- Identity Security
- Evaluates identity exposure relative to risk of compromise.
- Recommendations for strengthening MFA, access policies, and identity protection.
- Ransomware Protection
- Identifies attack vectors that can be exploited by ransomware.
- Implements recommendations for backup, network segmentation, and early detection.
- SaaS Security Vulnerability Assessment
- Monitors security configurations in cloud applications.
- Provides risk-based recommendations for data protection and access control.
- Zero Trust
- Analyzes current access policies and suggests improvements.
- Implements principles of least privilege and micro-segmentation.

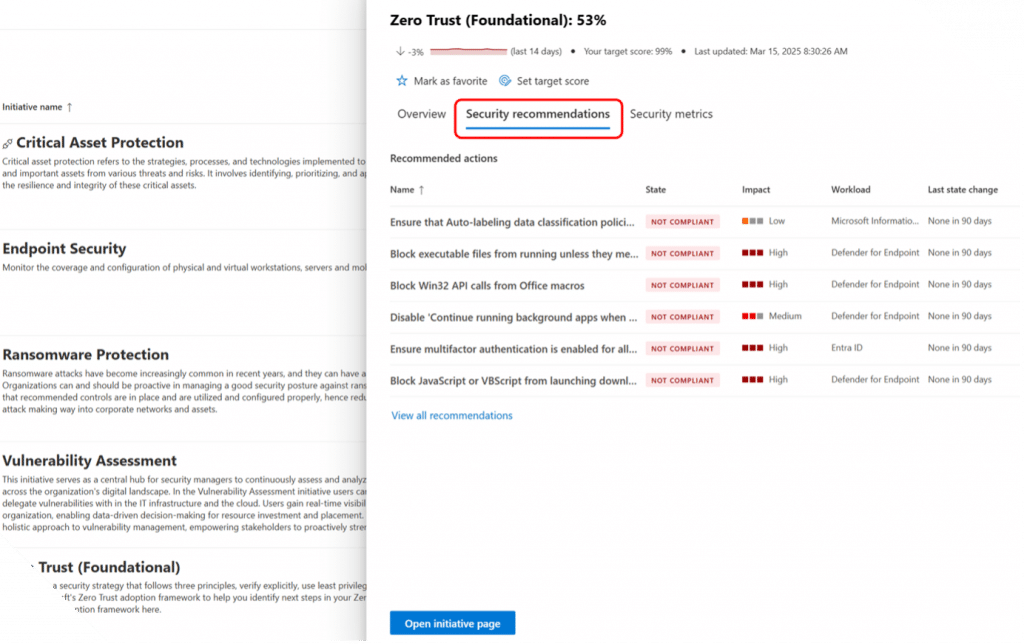
What does this mean for security leaders?
For security teams, this means a shift from reactive to proactive security.
Instead of constantly chasing the latest patches, teams can now focus on mitigating the biggest risks before they are exploited.
One of the biggest benefits of Defender Security Exposure Management is that it aggregates security exposures across Microsoft’s diverse workloads.
This includes:
- Defender for Endpoint, Defender for Cloud Apps, and Defender for Cloud – covering endpoint protection, SaaS applications, and hybrid cloud environments.
- Defender for Identity and Entra ID – securing identities and access control from compromise.
- Defender for Office and SharePoint Online – protecting sensitive data in collaboration tools.
- Defender for IoT and Defender External Attack Surface Management – monitoring external threats and unsecured IoT devices.
- Microsoft Information Protection – helping to classify and protect sensitive data.
But also external workloads such as: ServiceNow, Okta, Intune, Teams, Zoom, Slack, etc.
Conclusion
Microsoft has quietly delivered one of the most powerful security tools in a long time. With Defender Security Exposure Management, organizations can finally get the insights they need to navigate the modern threat landscape.
If your organization already uses Defender for Endpoint, check out this new feature—and start being more proactive about security today!

